
There is a strong reason to not use compromised and common password and Azure AD Password Protection is the right solution for organizations using Office 365 and It’s deployment effort is minimal.
I did testing in my lab for an Active Directory User who wasn’t synchronized yet to office 365/Azure and there were no licenses assigned to that user. At the end of this article you will be able to configure Active Directory to ban custom passwords using Azure AD Password Protection. Also Microsoft recently made this feature General Availability hence it is more promising now.
Prerequisites
- Azure AD Premium P1 Tenant.
- Global Administrator credentials.
- Installation of an agent on Domain Controller.
- Member Server – Install Proxy agent on member server and it must have .net framework 4.7 installed. This proxy member server will talk to Azure.
- Reboot will be required for Domain Controller and Proxy Member server where agent is installed.
Flow Diagram

Installation
Download these 2 binaries from https://www.microsoft.com/download/details.aspx?id=57071
- Install AzureADPasswordProtectionDCAgentSetup.msi to Domain Controller.
- This will result in installation of windows service AzureADPasswordProtectionDCAgent
- Install AzureADPasswordProtectionProxySetup.exe to Member Server.
- This will result in installation of windows service AzureADPasswordProtectionProxy
Note : Installation of both .exe won’t impact anything to your end users until you register the agent to Azure.
Configuration
Azure
- Navigate to Azure Active Directory > Authentication methods > Password Protection
- Make changes to these highlighted options and mention your custom banned passwords in the list.

Agent Configuration
Run these commands on Proxy Member Server :
- Register-AzureADPasswordProtectionForest -AzureCredential (Get-Credential)
It will execute tasks in backend and log these events on Proxy Member Server.
Run second command from Member Proxy Server as well :
- Register-AzureADPasswordProtectionProxy -AzureCredential (Get-Credential)

Testing
Before Registration of Agents :
- I added P@ssw0rd to banned password list on Password Protection Portal in Azure but I was allowed to change password to this one. Here are the event logs from DC Agent, which shows that we need to register agent before it will be enforced.
As soon as i ran both commands mentioned in ‘Agent Configuration’ section’ and now if i try to change password to P@ssw0rd then it throws me an error.

DC Agent shows that password wasn’t accepted because it is listed in global banned password list.
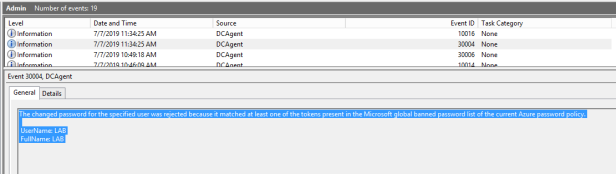
Logs
DC Agent
Launch Event Viewer and navigate to below section
Applications and Services Logs > Microsoft > AzureADPasswordProtection > DCAgent > Admin

Proxy Sever
Applications and Services Logs > Microsoft > AzureADPasswordProtection > ProxyService > Operational

Conclusion :
- Implementation of Azure AD Password Protection for Active Directory is very simple.
- If you want a phased approach then install DC Agent on a domain controller of a site, which has only pilot users and install proxy on same site as well. Perform all your testing and later deploy it on all domain controllers.
- I didn’t assign ‘Azure AD Premium P1’ license to Active Directory account and it was able to get the enforced banned passwords. It seem license validation doesn’t occur on individual accounts trying to change their password.
- Note : There could be some compliance reason to keep enough Azure AD Premium license but talk to your Account Manager, reseller or support for clarification.
Thank for your reading !